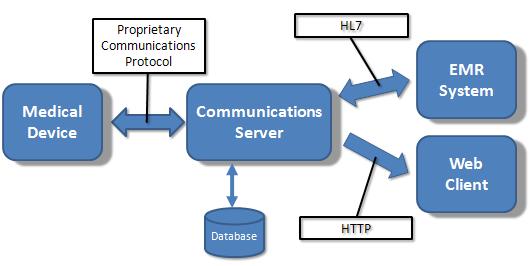
If you work with networked medical devices, Tim's post Medical Device Networks Trouble Industry is a must-read.
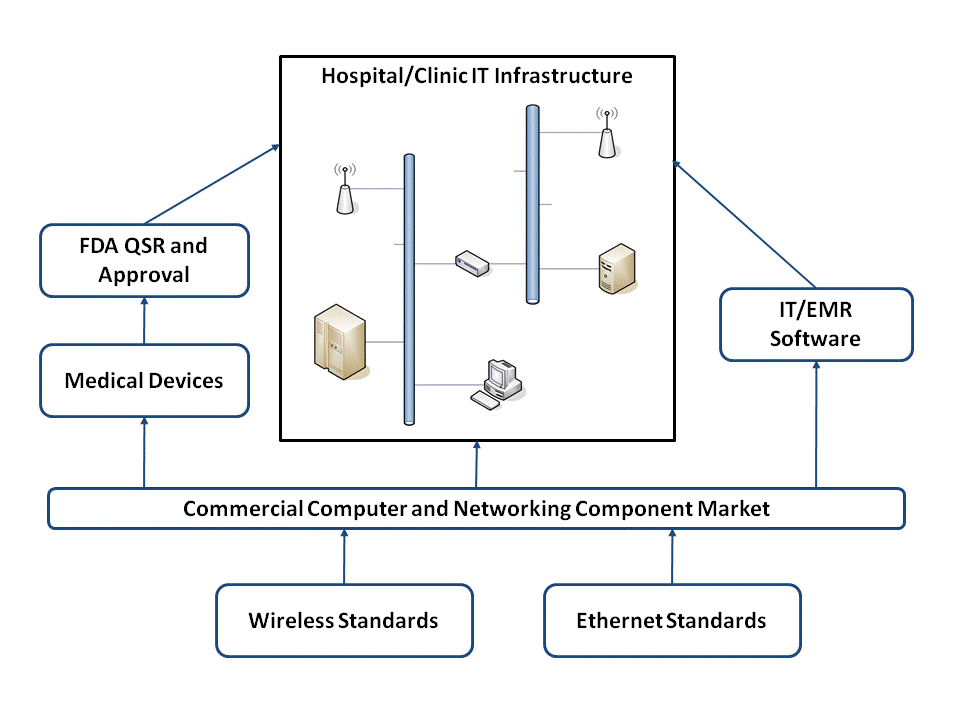
In order to better illustrate the bigger picture I thought this diagram might help:
This summarizes the relationship between the major players involved with integrating medical devices into an enterprise network and highlights some points I think are important.
- Only medical device manufacturers have to be concerned with the FDA regulatory aspects of placing computing and networking components into a medical environment. I've previously discussed some of the regulatory and verification/validation issues with Connecting Computers to FDA Regulated Medical Devices.
- All of the players -- hospital IT, medical devices, and IT/EMR software vendors -- deal with the same commercially available hardware and software components. This is simply due to the economy of scale. The medical industry isn't large enough create the quantities necessary to drive the cost out of most of these devices. We have to depend on the broader high-volume commercial marketplace in order to reduce cost.
- The medical device industry is involved in standards development, but at the end of the day its the broader market adoption that drives down the cost for everyone (see point #2). I think this is one of the main reasons why "the days of private medical device networks as we know them are over."
- FDA guidance and regulatory efforts in this area will always be in catch-up mode. As the technology and trends change they will be forced to evaluate the impact on patient safety after the fact. This is already happening -- as Tim points out (emphasis mine):
The bottom line here is that we can’t all look to the FDA to solve these issues that are the consequence of putting medical device systems on enterprise networks - when you do this, your enterprise network becomes part of a medical device.
Medical devices have been added to enterprise networks for years, yet IEC 80001 and the Medical Device Data Systems rule are still just drafts.
Some other thoughts:
- Private Medical Device Networks: Wireless networks are more often private. For wired networks "logically separate private networks through the use of network switches and routers" is more the norm. Since Ethernet took over in the mid 90s (anyone remember token ring?) most hospitals have not allowed private in-wall wiring installations.
- Enterprise Networks: One of the major challenges is just getting your private "logical" system installed on the hospital infrastructure. In addition to reliability, compatibility, routing, and bandwidth are just a few of the issues. One of the troubling aspects of this from a regulatory point of view is that there is no way for a medical device manufacturer to test all of the possible configurations that may arise in the field. The sustaining engineering and network variability issues are related problems.
- Hospital IT Culture: This is an issue that I have seen first-hand. A previous medical device I worked on used an embedded POSIX compliant UNIX variant. We ran into several hospital IT departments that refused to approve the medical device purchase because their policy would only allow computers running certain versions of the Microsoft OS on their network. This happened quite a few years ago. I can only hope that the integration philosophies of hospital IT departments have become more enlightened since then.
UPDATE (1/15/09): Here's another good article on this subject: Smoothing the Rocky Path of Interconnected Medical Devices.