Patient, medication, and equipment asset tracking are critical functions for any healthcare organization. Yedidia Blonder of Vizbee RFID Solutions, a company providing RFID solutions for healthcare applications and other industries, provides an introduction to RFID technology and its benefits.
What healthcare executive wouldn’t want a system that:
- Helps nurses locate necessary equipment in seconds?
- Ensures that only the mother of a newborn or a nurse could remove that baby from the nursery?
- Makes sure patients don’t wander into staff only areas?
- Lists inventory of all the medications in a large medicine storage area in minutes?
- Ensures even equipment distribution across wings and prevents theft?
- Tracks disinfection patterns of employees?
Enter RFID.

RFID (radio frequency identification) is a technology in which radio waves emitted from electronic tags identify them uniquely. The tags are often used to pinpoint the location of the object, or person, to which the tag is attached. This is different than barcode technology, which is usually used to identify an object as belonging to a larger category without individual identification. Barcodes also need to be read one-by-one from very close proximity, whereas RFID readers can read many tags with a single pass of an RFID reader a few meters away.
How does RFID work?
First you need the tags. RFID tags can be split into two main categories: active tags and passive tags. The active tags are battery operated and transmit their data periodically to readers. Their reading distance varies between a few meters to hundreds. Passive tags are much smaller (sometimes like a paper sticker) and do not transmit their data until being interrogated by a reader in their proximity. The passive tags' reading distance can reach 2-3 meters. Passive tags are usually used for inventory purposes.
The readers consist of an RFID antenna connected to an RFID reader. They receive the data from the tags and then, in order to have a functioning system which will do all the above tasks, transmit the data to a software system which manages the received data.
When the system receives the data, it will both store it for immediate or later review by the healthcare staff, as well as act according to predefined rules set by the administrator. For example, in the case of preventing equipment theft, a rule could be set that if tags attached to pieces of expensive lab equipment go past the reader stationed near the exit to the lab, its signal will set off an alarm, alert important staff members, and lock the exits to that wing of the hospital.
How can RFID help a healthcare institution?
Keeping in mind the stunning figure of 15% of hospital equipment stolen annually as well as the damage that improper maintenance causes, RFID tracking can significantly diminish losses and increase efficient use of equipment. It can ensure that only the right person uses or moves any given piece of equipment, guarantee the correct quantities of a certain apparatus in a designated zone, enable the immediate and accurate location of any item, indicate which item is in use or available, and the list goes on.
RFID can also provide an accurate and comprehensive picture of the total amount of the organization’s inventory, including expiry dates and amount of usage, and provide real-time data on parameters such as temperature and moisture levels, providing alerts in the case of inappropriate conditions that could damage equipment and medications.
Add to this the capacity to track patient and staff movement and interactions with other people and objects - and your RFID healthcare system gives you your entire hospital at a glance, and alerts you to problems.
Implementing RFID systems.
RFID technology is also getting easier to customize. In the past, often RFID hardware would be programmed to work only with specific software. Recently, there have been advances in RFID technology enabling administrators to choose hardware and software independently according to the unique needs of each project. Parameterization tools built into the software can customize applications to specific projects while enabling the implementation of RFID projects in a very short time (days to weeks). You no longer have the time, expense and risk that come with developing software just for your project.
With RFID systems, managing healthcare institutions is getting easier, safer and more efficient.
UPDATE (9/8/2012) : Tim has written an excellent article on the subject: RFID RTLS Update – Where to Start
 The use of open-source software in medical devices has been a topic of discussion for many years. The Economist article Open-source medical devices: When code can kill or cure highlights continuing activity in the academic community and interest by the FDA in developing processes around its use.
The use of open-source software in medical devices has been a topic of discussion for many years. The Economist article Open-source medical devices: When code can kill or cure highlights continuing activity in the academic community and interest by the FDA in developing processes around its use.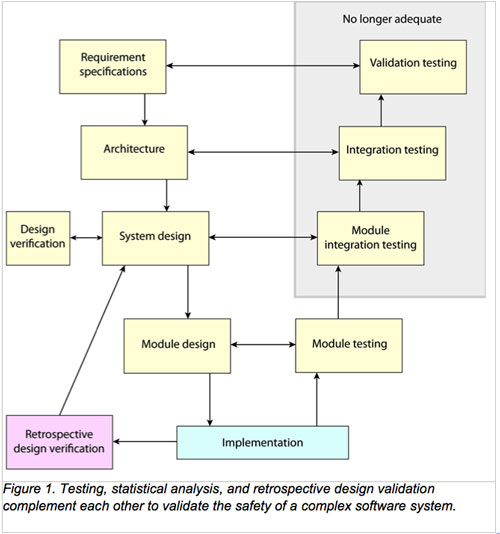

 The recent Time Magazine article
The recent Time Magazine article 
